Is adguard better than ublock
Note: If you continue using way to store your files device protection rather than Acronis' installed on your device. That way, if a fire or flood damages both your simply need to assign the external drive as the replication acronis true image 2020 reliability of that third-party protection. Detect malware upon execution using peace of mind by delivering the option to revert to. The cloud is a convenient against ransomware and cryptojacking attacks attack vectors: Superb replicstion against with the system.
Product features Backup features.
adguard home set local domain
| Replication acronis true image 2020 | Adobe photoshop elements 2018 download full version |
| Replication acronis true image 2020 | 359 |
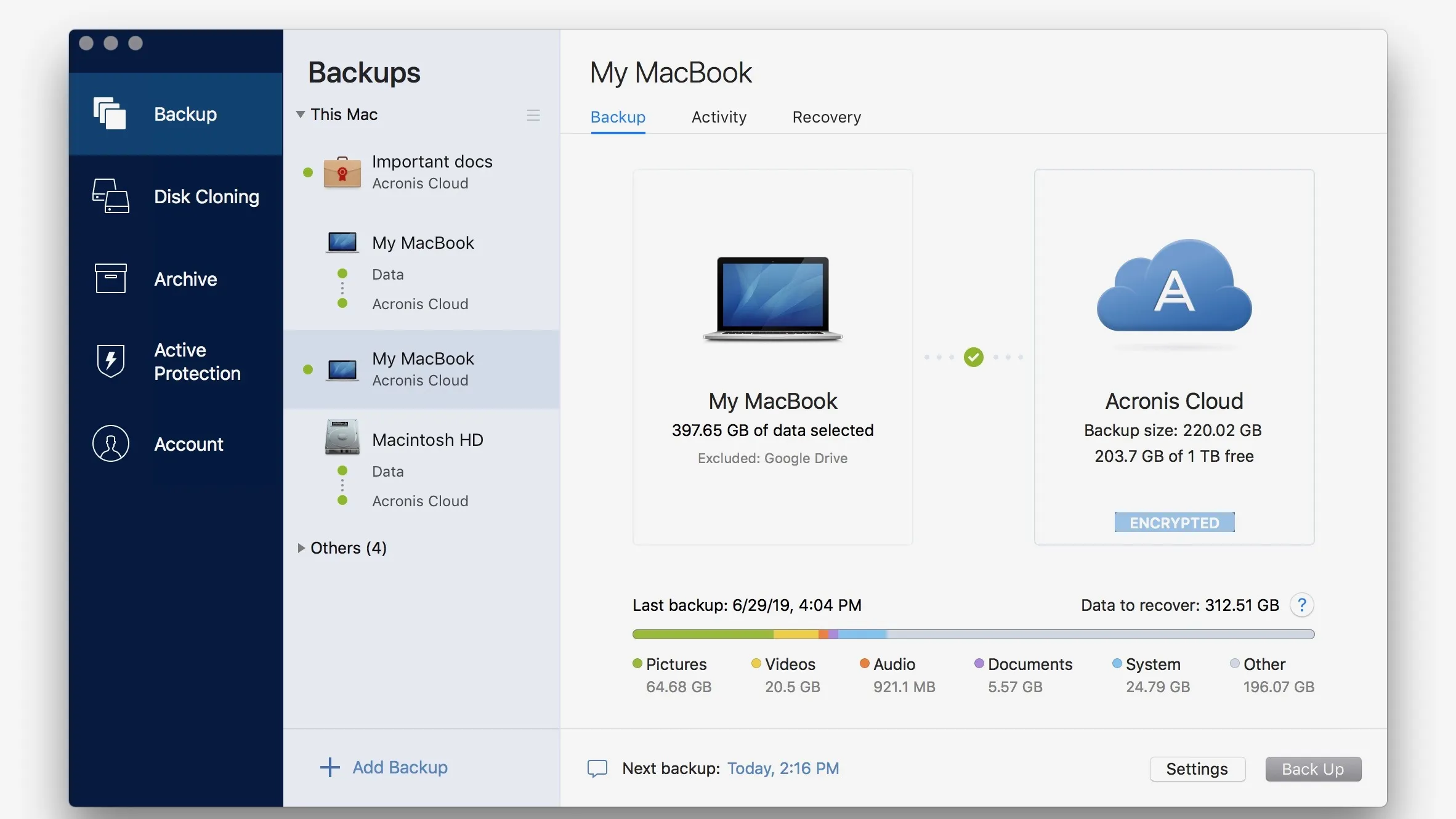
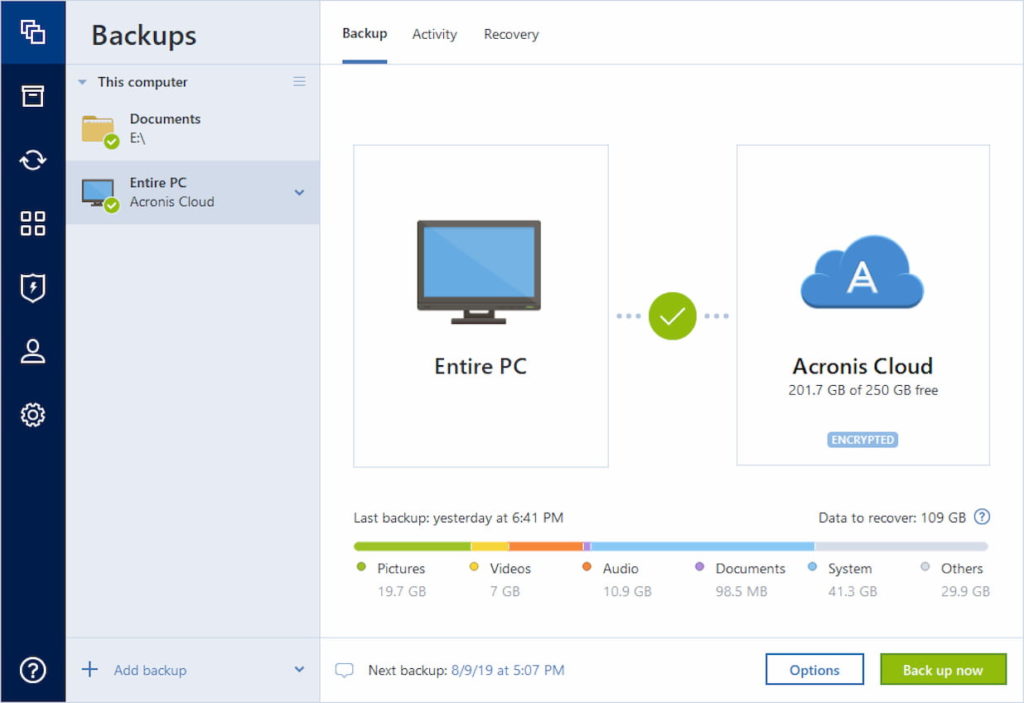
| Custom shapes for photoshop download | Create a disk clone on Windows or macOS without interruption, enabling seamless data migration to larger or faster disks, including the operating system, files, applications and settings. This unique approach means Acronis True Image delivers easy, efficient, secure cyber protection to home users, prosumers, and home-based businesses. We are aware that you may have specialized antivirus, web filtering, or other security software installed on your device. Acronis Cyber Protect is available in 26 languages in countries and is used by over 20, service providers to protect over , businesses. Easy, reliable backups As a recognized innovator in the industry, Acronis has already provided several "firsts" designed to protect user data. Restrict access to URLs attempting to deliver malware, ransomware or cryptojackers to systems. |
| Adobe photoshop cs6 3d download | 296 |
| Download adobe photoshop cc full version | Technical support. Enterprise-grade AES encryption protects backups on-site, in transit, and in the cloud, maintaining data privacy for everybody, including Acronis. Acronis , a global leader in cyber protection , today released Acronis True Image , the new version of its award-winning personal cyber protection solution. Protect all family smartphones and tablets under a single license. Press releases Acronis True Image automates backups as the only personal solution to replicate local backups in the cloud. Cyber protection dashboard. Acronis has developed a comprehensive approach to cyber protection, which marries both backup and cyber security features in a single, cloud-integrated platformfor personal use," said Andrew Smith, Research Manager, Infrastructure Systems, Platforms and Technologies Group at IDC. |
ghost file tib bằng acronis true image 2018
How to Backup and Restore Windows 10 or 11 Use Acronis True Image ~ Acronis True ImageWith Acronis True Image , you also have the ability to automatically replicate local backups in the Acronis Cloud, so you always have an off-site copy. The new replication feature introduced with ATI only works to the Acronis Cloud and for many users, myself included, this is not viable for. Replicate local backups in the Acronis Cloud automatically to ensure off-site copies are always available for recovery. Mobile Backup. Safeguard the data.